infohacking.com
- (New) ViewCVS Cross Site Scripting -
INTRODUCTION
"ViewCVS can browse directories, change logs, and specific revisions of files.
It can display diffs between versions and show selections of files based on
tags or branches. In addition, ViewCVS has "annotation" or "blame" support,
Bonsai-like query facilities, template-based page generation, and support for
individually configuring virtual hosts. (...)
(...) ViewCVS has been developed by the ViewCVS Group and is made available under a
BSD-type license. (...)"
(Quoted from: http://viewcvs.sourceforge.net/)
STATUS
Vendor contacted on December 17, 2003.
DESCRIPTION
From OWASP home page (Open Web SecurityApplication Project) I follow a link pointing to
Souceforge: http://cvs.sourceforge.net/viewcvs.py/owasp/
Once there a bad request (something like: http://cvs.sourceforge.net/viewcvs.py/owasp/a)
showme the "suspicious" error page. Then a simple request like this:
http://cvs.sourceforge.net/viewcvs.py/owasp/%3Cscript%3Ealert('OOPS')%3C/script%3E
showme the problem. Ironically while looking for information on application security,
I found an application security bug... ;-) No blames please, it's only a joke.
There's a classical XSS problem on ViewCVS software. It has nothing to do with
bugtarq ID 4818 (http://www.securityfocus.com/bid/4818), this is a new one.
This time the XSS is present in the error page generated by "ViewCVSException" in
"viewcvs.py" file.
SOURCEFORGE.NET
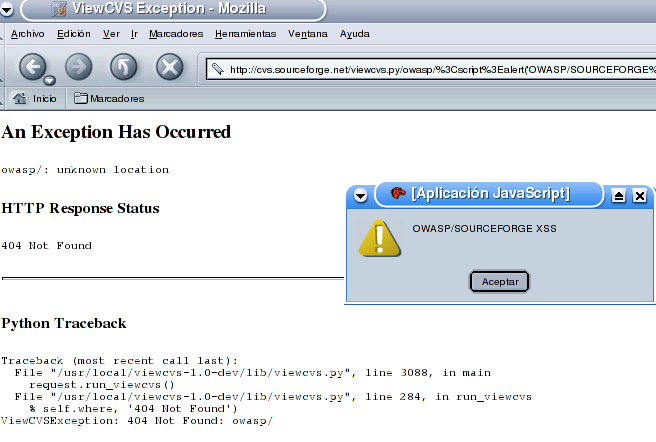
In the screenshot we can see that bug is present in the last version of ViewCVS
(viewcvs-1.0-dev),but probably it will be present also in previous versions.
This flaw is not a major bug by itself. The problem is (as always in this kind of
vulnerabilities) in the environment. ViewCVS main target installation are servers
with developing software to keep tracking of software version, etc. Those servers
are also primary targets for some kind of intruders. In some scenarios it could be
possible http session hijacking.
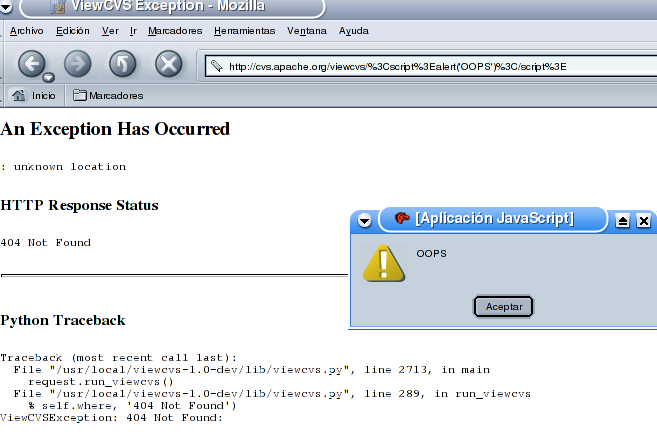
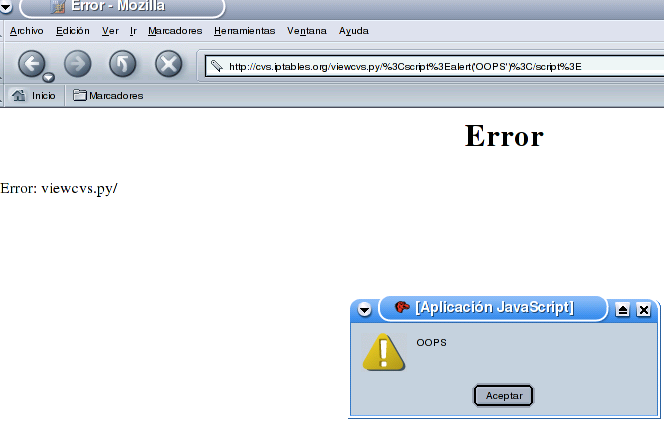
The problem has been proved to be present in other major websites that are using this
software:
APACHE.ORG
 IPTABLES.ORG
IPTABLES.ORG
etc...